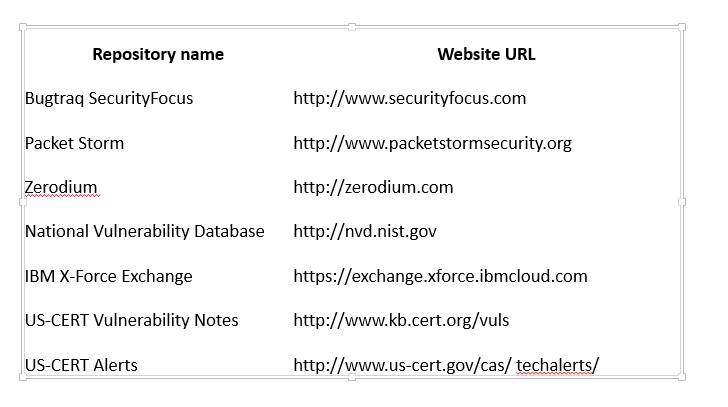
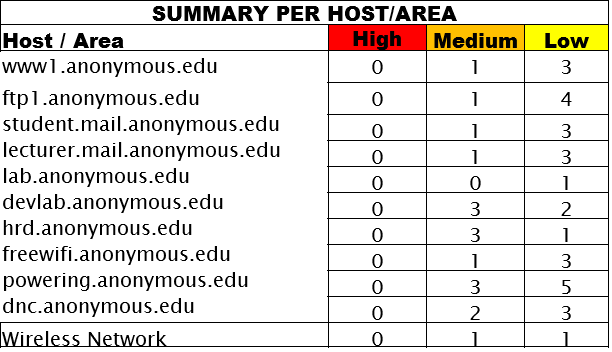
This week, we learn about using Maltego, and now I am gonna give a small tutorial on how to use it.
Maltego is a graphic application to detect any of domains, company or famous person in a form of a diagram. It is preinstalled in Kali Linux and it is very easy to use, easy to see relationships in a form of graphics and so on.
The aim of Maltego is basically for information gathering, the use is pretty simple, user just need to open the application and create a new project diagram, afterwards find the main information as the root of creating relationship diagram.
For example, you choose a domain and the domain is google.com.
Afterwards you just need to press all transform by clicking the root picture, and a branch of relationship will be shown. It is pretty simple and the data are accurate.
If a user want to see a relationship’s relationship of the data, they just need to all transform again from the specific branch.